Quickstart - product presentation
WALLIX Entreprise Vault
Safeguarding user logins and passwords is a critical aspect for businesses, as it addresses challenges associated with security risks and data protection.
Organizations prioritize countering these risks through encryption, access controls, and authentication mechanisms. WALLIX Enterprise Vault centralizes business passwords and sensitive identity data. This solution strengthens security through encrypted storage, reinforcing credential protection and optimizing the user experience.
By fortifying a secure data environment, WALLIX Enterprise Vault enhances collaboration within teams while safeguarding against potential threats. In essence, the platform serves as a comprehensive solution to the multifaceted challenges of credential management.
It is a cloud-based business tool, which means that the data is stored encrypted on a database accessible from anywhere and under the control of administrators.
Features and capabilities
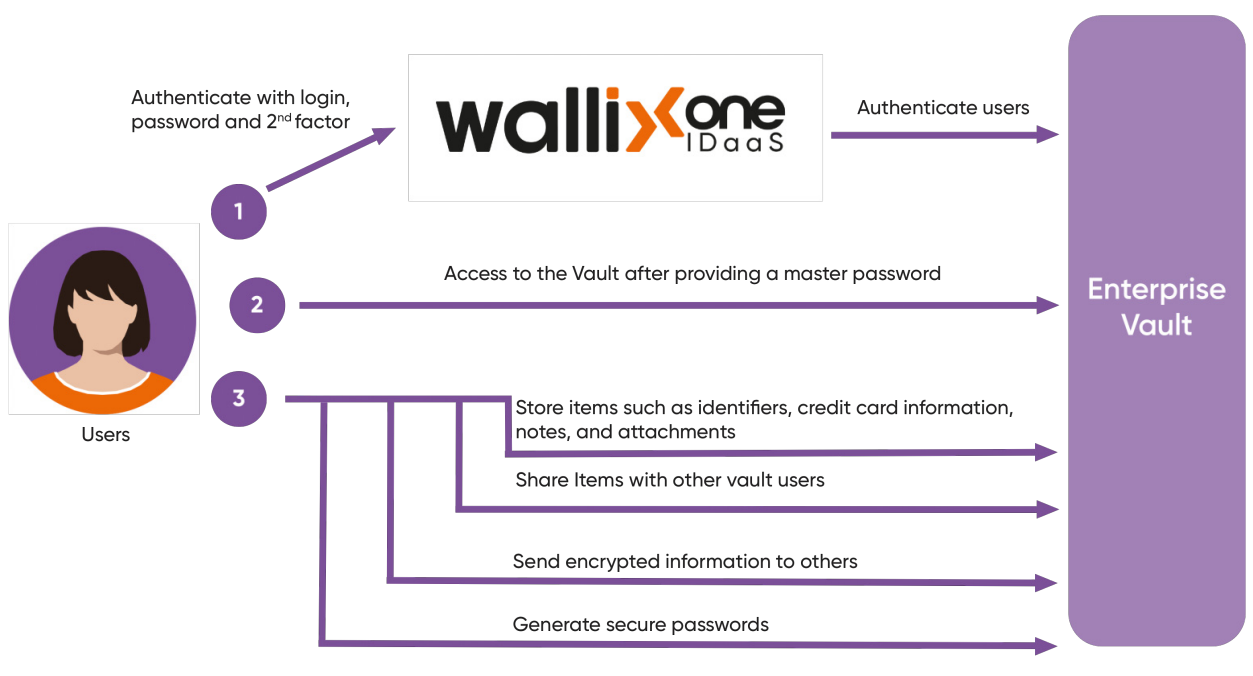
There are 2 populations which interact with the product.
End-User (quickstart guide)
- Zero-Knowledge encryption
- Encrypted data storage in a cloudbased environment
- Authentication with single or multifactor authentication
- Unlimited storage of items: identities, credit card information, notes, and attachments
- Secure credential sharing with users across your organization
- Direct encrypted sharing of text and files by email with non-vault users
- Password Generator
- Ability to change master-password
- Vault Health Reports
Administrator (quickstart guide)
- Account Lifecycle Management through Trustelem
- Entreprise Vault security policies
- Users’ master password recovery
- Event and audit logs
Technical Specifications
Four levels of encryption: User - Shared Vault – Items - Recovery
Application Range: Browser plug-in, Mobile Application, and Web Application
Available reports: Exposed Passwords, Password Reuse, Weak Passwords, Unsecured Websites, and Inactive Two-Step Login
Authentication methods: WALLIX IDaaS, Active Directory, LDAP
Silent Authentication: Kerberos / X509 authentication
Multi-Factor Authentication Methods (MFA): WALLIX Authenticator, TOTP, SMS/ Email OTP, Security Key U2F / FIDO
Native Integration of Directories: Active Directory, LDAP, Azure AD, G Suite Directory
Traceability: Complete logging and audit of access and authorizations
Extension: API and script publication to connect the platform to client environments
No Comments