Administration application
The Enterprise Vault admin application is dedicated to 5 usages :
- See Enterprise Vault usage
- Watch Enterprise Vault logs
- Define Enterprise Vault policies
- Manage Enterprise Vault existing users
- Manage Enterprise Vault existing shared vault
Do do so, you'll find 4 menus:
- Dashboard: a general overview of the existing vaults, with the clients used to access the secrets
- Users: information about the existing users (dates, vaults…)
- Shared Vault: information about the existing shared vault
- Logs: information about what happens on Enterprise Vault
- Settings: the global settings for Enterprise Vault
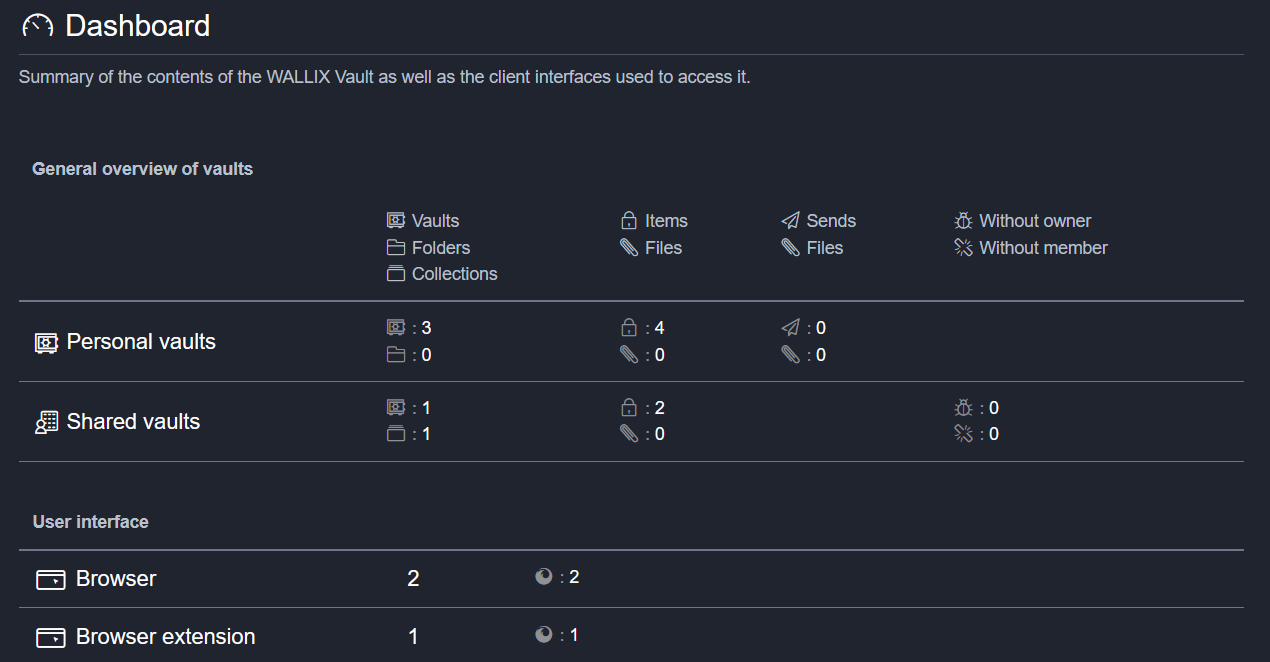
Dashboard
The dashboard tab displays a summary of the contents as well as the client interfaces used to access it.
This page gives a quick overview of Enterprise Vault adoption in your company. Among other things, you can see:
- Number of users (Personnal vaults > Vaults)
- Number of personal secrets (Personnal vaults > Items)
- Number of shared vaults (Shared vaults > Vaults)
- Number of shared secrets (Shared Vaults > Items)
- Type of client used (User interface)
There is one clickable information: the icon at the end of the user interface lines.
It gives details of the software used per user.
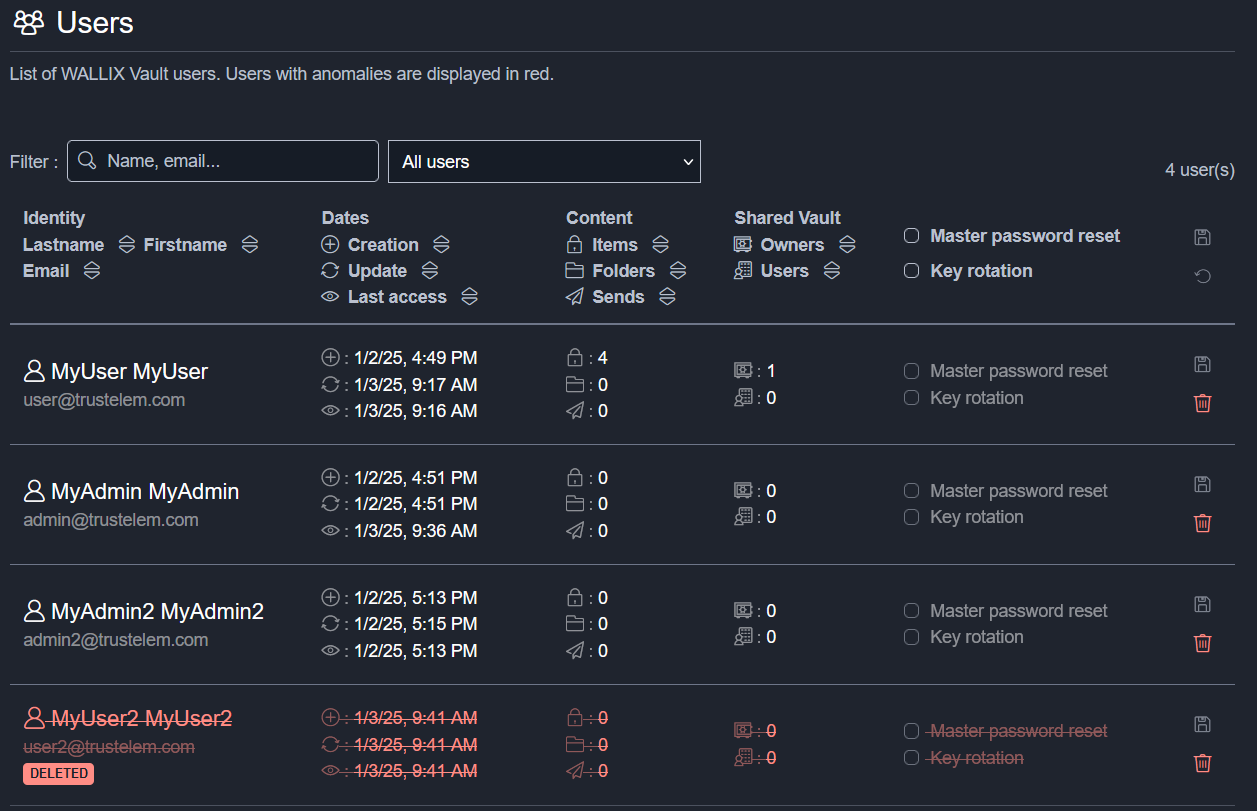
Users
The Users tab displays a list of WALLIX Enterprise Vault users. Users with anomalies are displayed in red.
This page shows, user by user:
- Creation, update and last access dates
- The number of personal secrets, as well as the number of personal folders and the number of existing sends
- The number of shared vaults where the user is owner or user
In addition, for each user it is possible to:
- Force a master password reset. In this case, the user must enter his old master password, then a new one.
- Force rotation of the user main encryption key, in addition to the master password reset.
- Delete the users and its secrets.
A user deleted on Enterprise Vault still exists on WALLIX ONE IDaaS.
Certain scenarios prevent the user from being deleted: for example, if the user is the only owner of the recovery key, or the only owner of a shared vault with members.
A user displayed in red has been deleted on the WALLIX ONE IDaaS side. But the user still exists on Enterprise Vault.
It is not possible to automate the user deletion on Enterprise Vault from WALLIX ONE IDaaS.
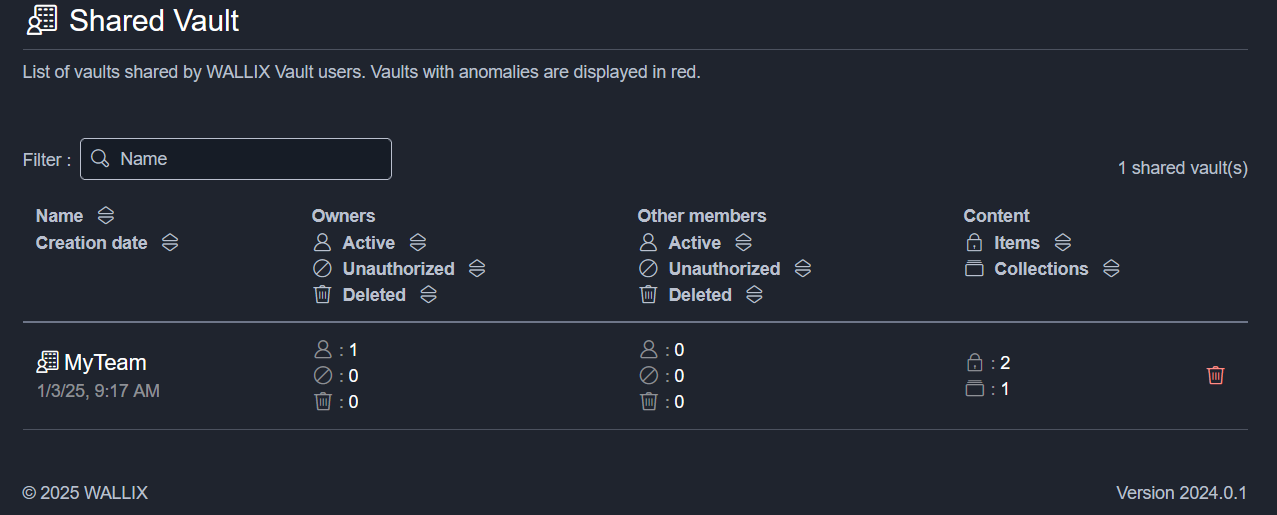
Shared Vault
This page shows, vault by vault:
- The creation date
- The active, unauthorized, deleted owners of the vault
- The active, unauthorized, deleted users of the vault
- The item and collection number
In addition, for each vault it is possible to delete the vault.
All owner/other member fields (active/unauthorized/deleted) are clickable, giving details of the users concerned.
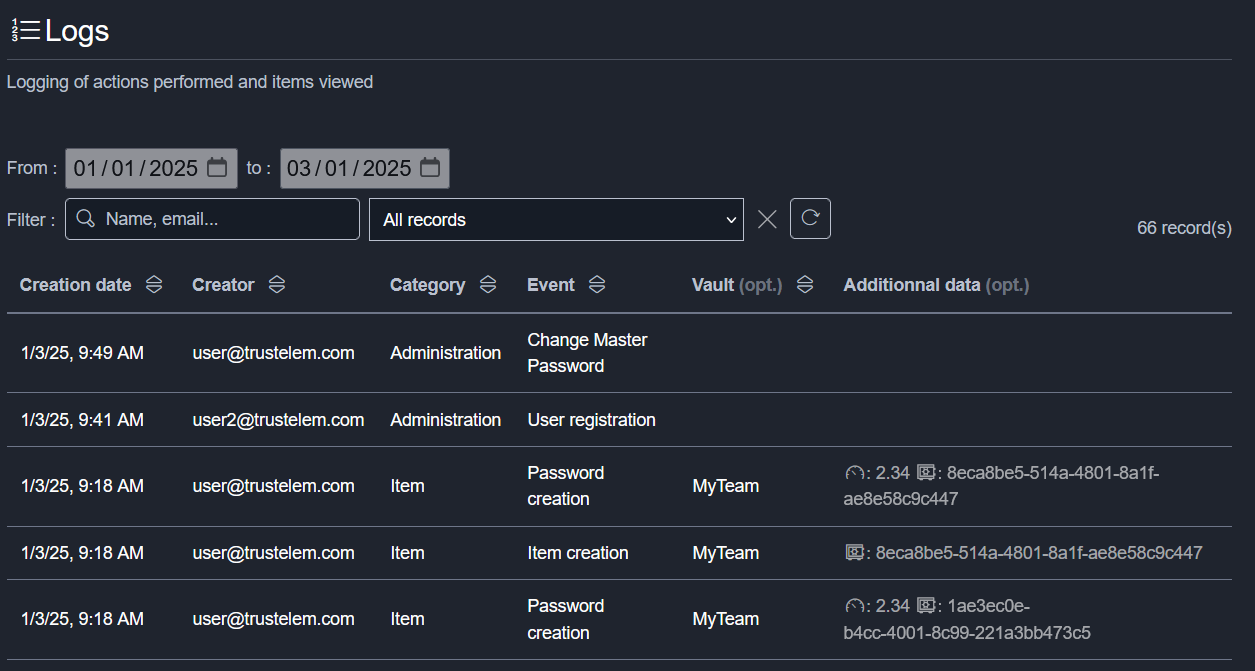
Logs
The Logs tab displays the logs of actions performed and items viewed
This page shows:
- The creation date
- The user who performed the action
- Action category (administration, item, collection, shared vault, domain, recovery)
- Event corresponding to the action (User registration, Item creation, Item access...)
- The name of the shared vault associated with the item, if the action is relevant
- Additional data, such as the strength of the password created, or the IDs of objects affected by the action
There are 3 types of filters for searching logs, which can be combined:
- A text field, allowing you to enter any information you wish to search for on the page
- A records field, for filtering by category or event
- A date field, allowing you to select the range over which you wish to examine the logs.
At present, it is not possible to extract logs (export or link with SIEM).
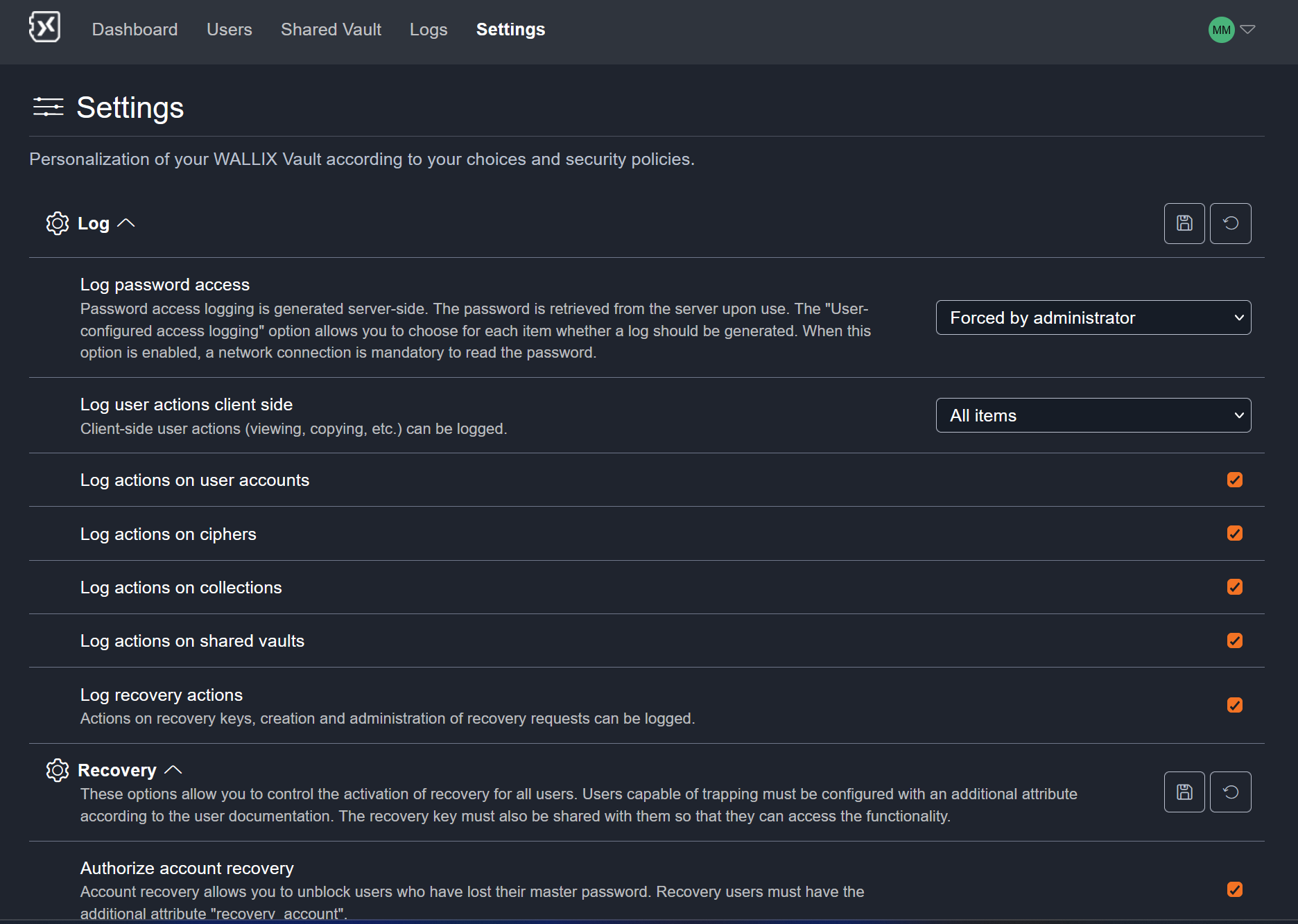
Settings
The Settings tab allows the personnalisation of WALLIX Enterprise Vault according to your choices and security policies.
Today there are 3 policies:
- Log: which information do you want to log?
- Recovery: do you allow master password reset ? Do you allow data recovery?
- Security: do you allow to list existing users in the forms that offer it in the user application?
Log
- Log password access: define if password access are logged or not
If password access are logged, it is not possible anymore to have an offline access
- Log user actions client side: define if actions done on user client (browser/plugin...) are logged
- Log actions on user accounts: define if actions related to accounts (creation, deletion...) are logged
- Log actions on ciphers: define if actions related to encryption keys (creation, rotation...) are logged
- Log actions on collections: define if actions related to shared vault collections (creation, deletion...) are logged
- Log actions on shared vaults: define if actions related to share vaults (creation, changes, deletion...) are logged
- Log recovery actions: define if recovery actions (requests, validation, quorum...) are logged
Recovery
When recovery is enabled, each item will be encrypted with an additional key dedicated to recovery.
This encryption is added the first time the user decrypts his items with his own key.
Consequently, even if the recovery is enabled, these operations can only be performed AFTER the user has made a new access.
So if you want to use them, it's important to activate recovery features from the beginning!
Security
- Allow all users of a shared vault to be displayed: when you add new shared vault members, you have to provide a valid email address of an existing vault user. But if this option is enabled, you'll have the list of existing users instead.
No Comments